In the previous article, “Mastering Azure DevOps Agents in Kubernetes - A Comprehensive Guide”, we explored the utilization of Azure DevOps agents operating within a Kubernetes cluster, which are dynamically scaled using KEDA. By building the agent from a Dockerfile, you can incorporate all the necessary software for your application’s build process. However, due to the agent’s location within a Kubernetes cluster and the discontinuation of Dockershim by Kubernetes, building a Docker image is not feasible.
In this post, we will delve into the use of Podman as a solution to build your Docker images, despite the Azure DevOps agent running within a Kubernetes cluster.
Building Docker Images without Podman
You can find the code of the demo on GitHub.
If your Azure DevOps agent isn’t running locally on your device or within Kubernetes, refer to “Mastering Azure DevOps Agents in Kubernetes - A Comprehensive Guide” for comprehensive instructions to get started. This guide also provides information on configuring the Azure DevOps pipeline to utilize your self-hosted Azure DevOps agent.
To test the process of building a Dockerfile with your DevOps agent operating within a Kubernetes cluster, create the following pipeline in your Azure DevOps project:
Ensure to use the pool in which your DevOps is running. Additionally, add a Dockerfile to your repository. For more information on Docker and Dockerfiles, see “Dockerize an ASP .NET Core Microservice and RabbitMQ”.
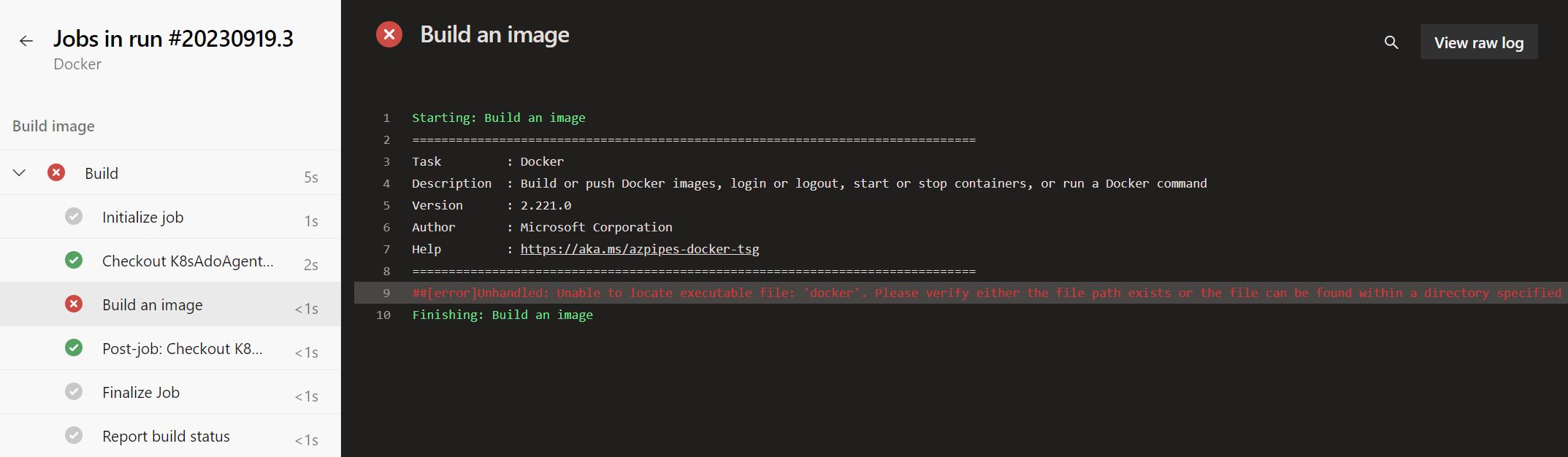
Upon running the pipeline, you’ll encounter an error message akin to the one displayed in the following screenshot.
Install Podman in your Azure DevOps Agent
You can find the Dockerfile of the Azure DevOps agent on GitHub.
The installation of Podman might seem daunting if you’re unfamiliar with the process, but it is actually quite straightforward. Initially, you will need to manually add the Kubic repository, as it is not included in the default Ubuntu repository.
Following this, install Podman along with the fuse-overlayfs:
Lastly, it is necessary to add a volume. Without this step, you will encounter an error message when running the agent, as Podman will be unable to mount the required volume.
These are the only modifications needed for the Dockerfile. The complete Dockerfile looks as follows:
You can now execute the DevOps agent locally using the command outlined in the last post. Remember to include the –privilege flag to operate the container in privileged mode. Failure to do so will result in an error message when attempting to build a Dockerfile with your agent.
Build Dockerfiles with your Azure DevOps Agent running in Kubernetes
Before proceeding with building your Dockerfile using the newly configured agent, it is necessary to update the pipeline. As we have transitioned to using Podman, the Dockerfile must be built using Podman. Replace the Docker task in the pipeline with the following code:
Ensure to update the path to your Dockerfile accordingly. If you haven’t deployed your agent to Kubernetes, see “Mastering Azure DevOps Agents in Kubernetes - A Comprehensive Guide”.
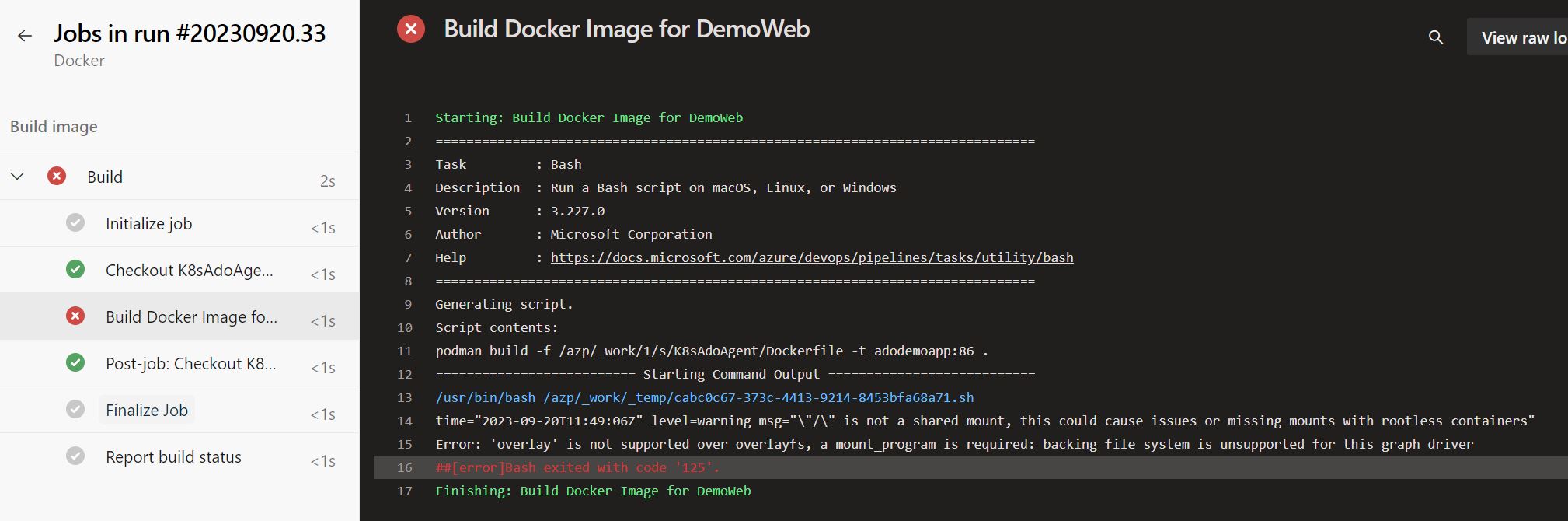
Upon running the pipeline, you will likely encounter the following error message:
This error arises due to Podman not operating in privileged mode.
Run your Azure DevOps Agent in Privileged Mode within your Kubernetes Cluster
To fix the previous error, it is necessary to operate your Kubernetes agent in privileged mode. This can be achieved by incorporating the following code into the specification section of your container:
The complete keda-scaled-jobs.yaml file should appear as follows:
To apply the file, use the following command. From this point forward, your Azure DevOps agent will operate in privileged mode:
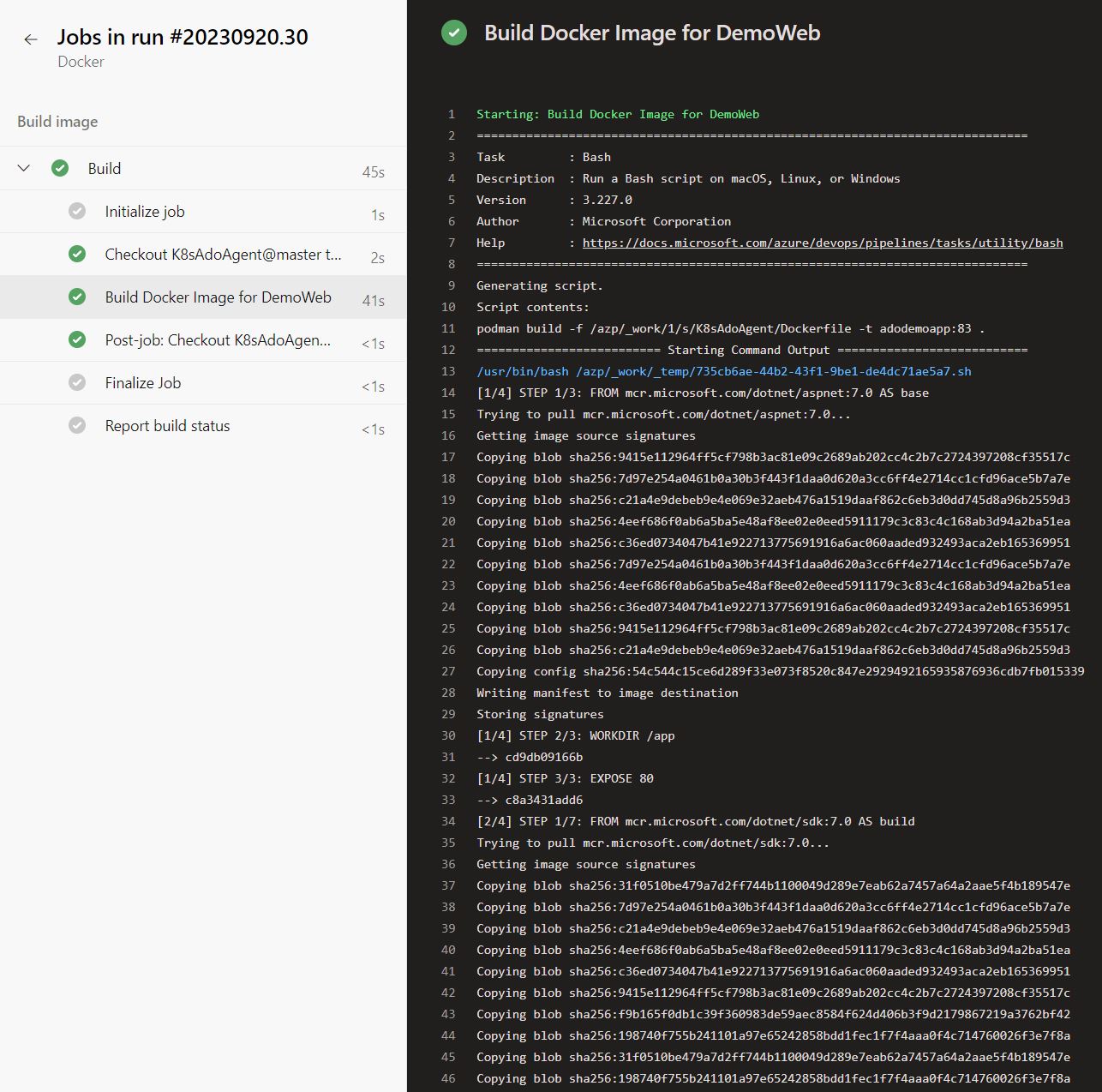
Upon running your pipeline again, the Dockerfile should be successfully built.
Considerations when Building Docker in Docker with Podman
It is important to note that, typically, the aim is to operate your pods and containers with the minimum privileges necessary. Running the Azure DevOps agent in privileged mode could potentially pose a security risk. However, I was unable to operate it in a non-privileged mode.
If anyone has insights on how to operate the container in a non-privileged mode, your contributions in the comments below would be greatly appreciated.
Conclusion
In conclusion, this blog post has provided a comprehensive guide on how to use Podman to build Docker images with an Azure DevOps agent running inside a Kubernetes cluster.
We have explored the process of installing Podman, running the Azure DevOps agent in privileged mode, and updating the pipeline for Dockerfile construction.
However, it is important to note that running containers in privileged mode can pose potential security risks, and it is generally recommended to operate with the least privileges possible. If you have insights on operating the container in a non-privileged mode, your contributions would be greatly appreciated.
You can find the code of the demo on GitHub.


Comments powered by Disqus.